AI-based Cybersecurity Risk Assessment

Domain #1
Sensitive infrastructure protection
Challenge 1.1 Development of cybersecurity solutions for sensitive infrastructure protection
![]()
Demonstrator
![]()
Open Call #2 laureate
Description of the project
AIRA, an innovative platform aimed to automate evidence-based security risk assessments. As a SaaS platform AIRA enhances investigation accuracy, reduces time, and increases productivity in proactive risk discovery and breach response. With AIRA software, organizations can respond to cyberattacks, conduct full-scale compromise assessments in less than 10 days, and discover initial findings in just 1 hour.
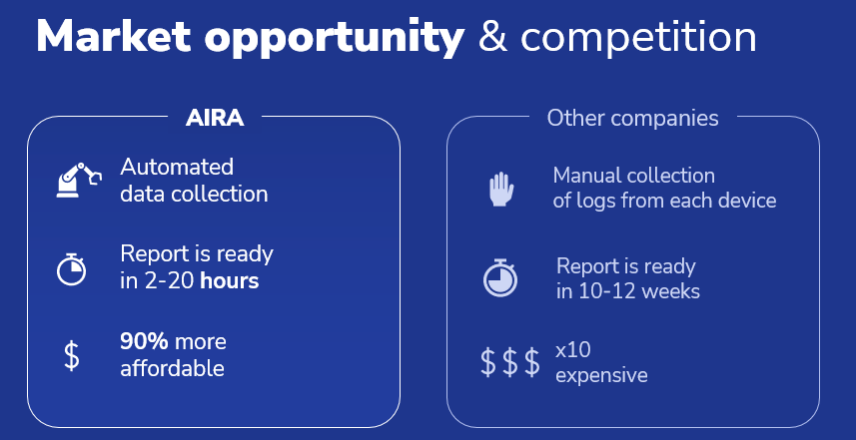
AIRA is a single tool that streamlines this process with automated artifact collection and data enrichment, built-in static and dynamic analysis, pattern comparison, report generation, and risk scoring. This enables the investigation to be completed in a matter of hours with automation or in a matter of days with the analyst’s involvement. While the industry average time is nearly 2 months.
ISSP has developed artifact collectors for the Windows environment, in-cloud secure architecture with encrypted storage and the analysis engine including web interface for the analyst. However, there is need to finish Artifact collector for Linux and Mac, the engine for UNIX systems and the analyst canvas for editing findings and data manipulation. This will be done within this project.
After the development completion, AIRA software will be available as a SaaS subscription for MSPs and enterprises. The project team will be focused on expanding AIRA to Linux and MacOS devices to increase market potential and create a strong competitive advantage.
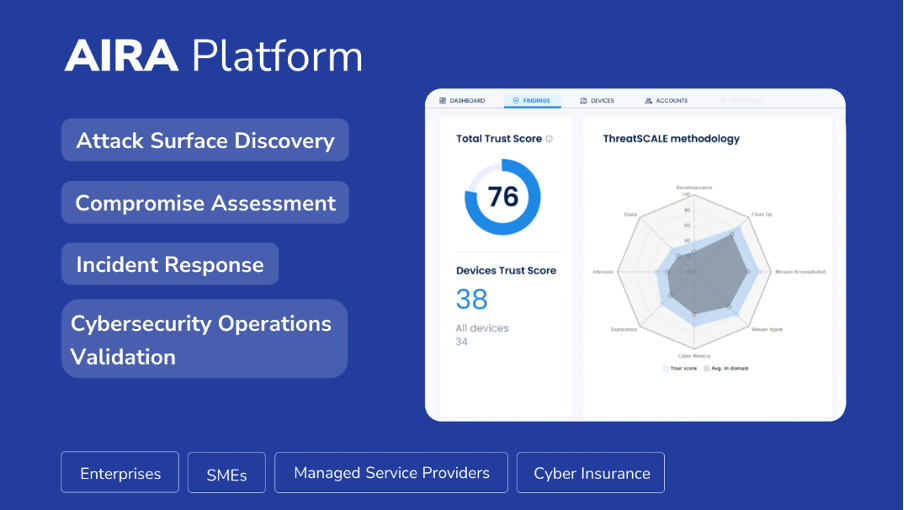
At ISSP we used 15 years of experience investigating and researching sophisticated attacks across various organizations and industries to build AIRA – a risk assessment solution that reduces the time, resources and costs associated with a Compromise Assessment by up to 70%. AIRA provides automated cybersecurity assessments through a combination of automated log data collection and analysis, our platform delivers a comprehensive report detailing specific risks and areas of concern for businesses. Regular cyber assessments will help to prevent breaches, respond to cyber incidents quicker and reduce the attack surface.
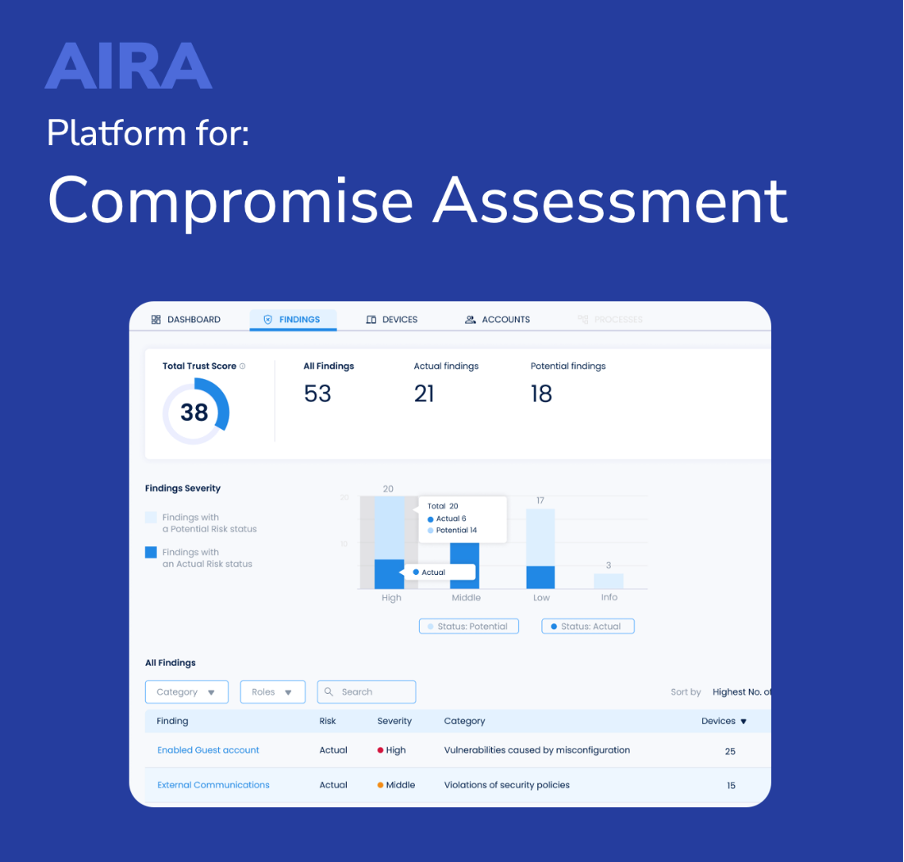
AIRA, an innovative platform aimed to automate evidence-based security risk assessments. As a SaaS platform AIRA enhances investigation accuracy, reduces time, and increases productivity in proactive risk discovery and breach response. With AIRA software, organizations can respond to cyberattacks, conduct full-scale compromise assessments in less than 10 days, and discover initial findings in just 1 hour.
Mid-term project update
Vulnerability Models: Defined 7+ models for MacOS, 10+ for Linux, aligning with MITRE ATT&CK for robust threat analysis.
This comprehensive modeling approach ensures that potential vulnerabilities across different operating systems are thoroughly examined, providing a strong foundation for effective threat analysis based on industry-standard framework MITRE ATT&CK.
Efficient Data Collection: Streamlined artefacts collection for MacOS and Linux, ensuring comprehensive insights through Osquery.
By optimizing data collection through Osquery, we provide a more efficient and thorough examination of system artifacts, enhancing the depth and accuracy of insights into potential vulnerabilities on both MacOS and Linux platforms.
Unified Tool: Implemented a unified data collection tool for MacOS, supporting both x86 and ARM architectures.
The implementation of a unified tool not only simplifies the data collection process for MacOS but also ensures compatibility with both x86 and ARM architectures, providing a versatile solution that caters to diverse system environments.
Workflow Scalability: Outlined an end-to-end workflow, selecting OSQuery, Elasticsearch, Kibana, PostgreSQL for scalability.
By structuring an end-to-end workflow with scalable technologies like Osquery, Elasticsearch, Kibana, and PostgreSQL, we ensure that the platform can adapt and handle increasing demands while maintaining the efficiency of data processing and analysis.
Pre-Processing Services: Initiated services for both MacOS and Linux, enhancing analytical capabilities.
The introduction of pre-processing services for both MacOS and Linux enhances the platform’s analytical capabilities, enabling more nuanced and sophisticated analysis of collected data to identify potential threats with greater accuracy.
Integration Success: Demonstrated Proof of Concept models for Linux, integrating them into the visualization process.
The successful integration of Proof of Concept models for Linux into the visualization process solidifies the platform’s ability to seamlessly incorporate and display critical threat information, improving the overall effectiveness of the cybersecurity solution.
User-Centric Access: Launched End-user Client for read-only access, with ongoing UX improvements.
The introduction of an End-user Client not only provides read-only access to users but also reflects our commitment to a user-centric approach, with continuous improvements in the user experience to ensure accessibility and ease of interaction.
Integration Success: Demonstrated Proof of Concept models for Linux, integrating them into the visualization process.
The successful integration of Proof of Concept models for Linux into the visualization process solidifies the platform’s ability to seamlessly incorporate and display critical threat information, improving the overall effectiveness of the cybersecurity solution.
User-Centric Access: Launched End-user Client for read-only access, with ongoing UX improvements.
The introduction of an End-user Client not only provides read-only access to users but also reflects our commitment to a user-centric approach, with continuous improvements in the user experience to ensure accessibility and ease of interaction.
Administrative Enhancements: Improved admin and analyst views, adding markdown support for quick template additions.
Enhancements to admin and analyst views, coupled with markdown support, contribute to a more user-friendly administrative experience, allowing for quick and efficient template additions and customization to meet specific cybersecurity needs.
Rigorous MVP Scope: Defined precise scopes, covering package creation, log file collection, Osquery commands, and automated cloud upload.
The definition of precise scopes ensures that the MVP encompasses critical aspects, including package creation, log file collection, Osquery commands, and automated cloud upload, guaranteeing a robust and comprehensive cybersecurity solution.
Agile Development: Maintained agile development, ensuring quick responses to challenges, positioning AIRA as a proactive cybersecurity solution.
The commitment to agile development methodologies ensures swift responses to emerging challenges, positioning AIRA as a proactive and adaptive cybersecurity solution capable of addressing evolving threats in real-time.
Final project update
AIRA – an innovative solution for automated, evidence-based security risk assessments. Developed by ISSP, a cybersecurity service provider, in collaboration with Estonian ENKI Consulting, AIRA is a cutting-edge Software as a Service (SaaS) platform designed to enhance investigation accuracy, reduce time, and increase productivity in proactive risk discovery and breach response.
AIRA concentrates on discovering attack surface, identifying vulnerabilities, and evaluating security setups, with a special focus on small businesses.
The project has achieved significant milestones, completing Research & Development phases for MacOS and Linux. Building on this foundation, we’ve implemented new configuration and vulnerability assessment models using a new architectural approach, ensuring a robust cybersecurity framework.
Expanding our web-platform capabilities, AIRA now supports not only Windows but also Linux and MacOS. This inclusivity extends to easy integration of new models directly on the AIRA platform, enhancing its adaptability to evolving cyber threats.
What are the main advantages of AIRA?
1. High efficiency: By automating artifact collection, data enrichment, and analysis, AIRA expedites investigations, reducing the time required for comprehensive assessments from months to hours.
2. Comprehensive Insights: AIRA offers a clear picture of an organization’s cyber posture, shedding light on previously undetected vulnerabilities. Modern risk assessment tools, like the AIRA platform, mark a significant leap forward in cybersecurity. By receiving automation and data-driven insights, businesses can proactively mitigate cyber risks, fortify defenses, and safeguard their digital assets against evolving threats. In perspective, it helps them to be more profitable and avoid financial and reputational losses.



